Client News, Digital Marketing Advice, Philippa's Blog
South African Cyber Crime & Cyber Threats To Look Out For
It’s Not Just In the Movies or CSI
Picture the Scene…
You’ve been waiting, planning and getting so excited for this very day.Months and Months of preparation have been put into a brand new product release that is going to take your Spa to new heights.Your Social Media team (That is your 18 year old daughter and 15 year old son); have been marketing this for ages. They’ve Shared, Liked, Loved and #Hashtagged like Social Super heroes. All the content, images and articles have been building up to this momentous occasion.
You wake up in the morning nervously, excited for the incoming tidal wave of orders and inquiries.
Shortly your partner calling you in hysterics yanks you into reality. And all you can make out from the poor women’s ramblings is…
IT’S BEEN HACKED!!
OUR WEBSITE IS DOWN!!!!
You try staying calm but now the panic starts kicking in…
Your Mind Starts Racing…
“My project release is ruined!!”
“Who Did This?”
“How Did This Happen?”
“Why Did This Happen?”
“How Can I Fix This?”
“What is this going to do to my business…?”
Reality of The Modern World
Fear is not our preferred way to educate or promote Safety, but we have to face the reality of our modern times. With everyone heavily reliant on the Internet for anything and everything, cyber crime and especially website hacking is an ever-growing issue. The Stats particularly in South Africa are rather scary.
Well we need to talk about it. Let’s get those common questions out there and maybe put your minds at ease by answering them.
So what is Cyber Crime?
Cyber crime is known as a crime to which, a computer, and Internet or computer technology has been a part of. Although this is a very broad definition basically if any harm is enforced upon a victim directly or indirectly, using modern telecommunication networks, it’s a Cybercrime.
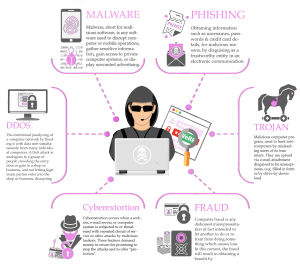
What Types of Cyber Crime must I look out for?
That Just happens in the Movies & In America, Doesn’t It?
Well, you are very wrong there. According to the South African Banking Risk Information Centre (SABRIC) – “South Africans lose in excess of R2.2bn to Internet fraud and phishing attacks annually.” According to a report done by Norton (The leading antivirus software company in the Country). South Africa has the third highest number of cyber crime victims worldwide.
Wow! That is Scary! But Only I know my Passwords, So my Website and Data is safe.
Hackers are very crafty and have many ways to get information from you. Here are five simple ways they can get your details.
Firstly more than 60% of people use the same username and password for all their accounts. Hackers run programs that enter stolen username and password details on tens of thousands of sites until one hits. Then they have access to your accounts and credentials. If you use the same username and password on all accounts, that can leave you extremely vulnerable.
Do you use Public WIFI? Well they have programs to monitor public Wi-Fi traffic and intercept information such as you typing in a username and password.
There’s something called Phishing. And they have two ways of Phishing for private information.
Tab Nabbing: Fake sites that look legitimately designed to steel your login details before redirecting you to the real site.
Key Logger Attacks: Dodgy emails that when open install code which records and sends all you data to the hackers.
Lastly Brute Force Attacks: Hackers use tools that can crack your password by simply entering different combinations and types of passwords over and over until it’s cracked; these tools can easily be downloaded for free. So within 24 hours, most passwords are cracked and the hacker has access.
If you insist on using archaic static password, please use a long complicated one. And don’t save your passwords in a folder on your computer.
Ok I changed my Password. I’m Safe Now right?
That is definitely a good start. Getting personal anti virus software is another advised step. But if your Website is not fully protected itself, it is still vulnerable to hacker attacks.
Ok that’s Ridiculous there are millions of websites, they can’t possibly find mine.
I’m Sorry to disappoint you. Google Dorking, also known as Google Hacking, enables Hackers to find sensitive data or evidence of site vulnerabilities. Basically they enter a search term into Google and find websites, which may have vulnerabilities somewhere on the site. Programs such as Acunetix then definitively pinpoint a site that is vulnerable and can be attacked.
I’m afraid to ask, what they will do once they’ve found my site?
It’s not pretty. Most commonly, they will try Inject a type of programming code called SQL( A programming language designed for managing data in a database) into your websites code. This will allow them to steal information stored from your websites database.
And, that’s how easy it is. Within minutes they can search for, download and use a couple of automated tools, access websites which are vulnerable to this type of attack. And take what info they want.
*While most high profile companies’ websites will be protected from this type of attack, the fact that Sony’s website and the personal information of its customers was stolen in a manner similar to this, shows just how vulnerable the web is.
And if all attempts fail, they will employ something called a Ddos attack. Basically they bombard your site with so many requests that it can’t handle the load and crashes (shuts down). And When the system is offline, the hacker proceeds to either compromise the entire website or a specific function of a website to their own advantage. This can be done easily from their Smart Phones.
But What Does a Hacker want with my Website, I’m Not A Standard Bank?
The major motivations for hackers to target any site are to; Gain traffic to their own sites, financial gain, and practice/fun and not to mention the recognition for being “so clever”.
Here is a list of how they will use your little ol’ website.
- Defacing your Site / Taken Offline
In some cases hackers replace your content with their own.
- Sending Spam
Hackers send mails for their personal gain. The mails will originate from your domain and IP address, and your paying for it, financially and reputationally.
- SEO Spam
Using your website in many ways to increase their Websites SEO ranking.
- Malicious Redirect
Using your website in many ways to increase their Websites SEO ranking
To funnel traffic to their malicious websites.
- Host Phishing Page
Phishing pages attempt to fool the visitor into providing sensitive information,
In others they try to capture your username and password to various sites, including your WordPress site if you’re not careful.
- Distribute Malware
Once they have compromised your site, attackers can install malware that in turn installs malware on your website visitor’s computers without their knowledge. This is an incredibly scary proposition for you as a site owner.
If Google detects that it is happening they will flag your site via their safe browsing program. This will cause your SEO traffic to drop significantly.
- Ransomware
Is malicious software that blocks access to your website and demands that you pay a ransom in return for having access restored. This kind of attack has been receiving a lot of attention late.
- Host Malicious Content
Hackers will very often use your web server to host malicious files that they can call from other servers. They are essentially quietly using your hosting account as a file server.
- Referrer Spam
If you use Google Analytics you are likely familiar with referrer spam. Referrer spam is bot traffic to your site set up to look like it is coming from a fake referrer. The spammer is trying to get the website owner to check out where the traffic is coming from, driving traffic to the site.
WOW! I had no Idea! What Can I Do to fix this once it’s been hacked??
The plain fact is prevention is always and we mean always, better than the cure, because the effects of hacking extend way beyond just your site not working, or being used for nefarious purposes.
Reputation & Trust of your clients can be forever spoilt, not to mention your SEO Ranking can be permanently damaged. But if it does occur don’t panic, you can fix it.
Warning this may be confusing
- Changing your passwords for website logins, database, ftp, etc.
- Make a backup of the site and download it for inspection
- Examine log files and other data to determine how and when the website was hacked
- Examine the software extensions used on the site and ensuring they are up-to-date and do not have any known vulnerabilities
- Review any custom software code (if applicable) for any obvious security flaws
- Clean the site and putting it back online.
It is very important if at all possible to understand how the site was hacked so that it can be properly cleaned.
Um…Yes that’s VERY Confusing, English Please!!
Ok Our Advice,
Get smart and you’ll never have to worry about it.
When you are shopping for your website developer or hosting company (A Local hosting service provider is always best).
Make sure they have
- A quality development team.
- Front End and Back End Security Measures in Place
- An amazing support team to take care of all that Scary Confusing stuff.
- And make sure you get monthly weekly reports to monitor how they are keeping an eye on everything.
With websites we always believe spending that extra bit for quality is always better. Because rather pay that little bit more and have the quality and safety then have to spend the thousands upon thousands of Rands in losses and recovery fees.